Researchers at Trend Micro report that online criminals are spamming out ransomware to potential victims in South Korea disguised as…. eggs.
Well, to be clear the file attached to the emails is an .EGG file – a compressed archived file format (like .ZIP, .tar, .LZH, .ARC, and a gazillion others).
Most of the world doesn’t commonly use the .EGG archive format. But in South Korea, it has been tremendously popular ever since South Korean company ESTsoft developed the format in 1999, and released its multi-format compression utility ALZip the same year.
As a consequence, many South Korean users might find it odd if an archived file was sent to them by a friend or colleague in an archive file format other than .EGG.

As Trend Micro’s analysts explain, the criminals behind a GandCrab ransomware campaign seem to be deliberately targeting South Korean users, spreading the malware within an .EGG attachment in an email that users might be tricked into opening without properly considering the consequences:
In our analysis of the samples, the attached EGG (TROJ_GANDCRAB.TICABAK) contains three files: two shortcut .lnk files (LNK_GANDCRAB.E) that are disguised to appear as documents, and an .exe file that will disappear once the user decompresses the EGG file. Within the .lnk files, “VenusLocker_korean.exe” is inscribed, which could mean that the VenusLocker group was behind the distribution of spam mails.
The spam mail is under the guise of an investigation on an “e-commerce transaction” violation. In English, an excerpt from the email body roughly translates to “’Unfair e-commerce notification’ has been filed against your head office, I will let you know that I am going to do it.” Meanwhile, the attached EGG file is named “Notification of e-commerce violation.”
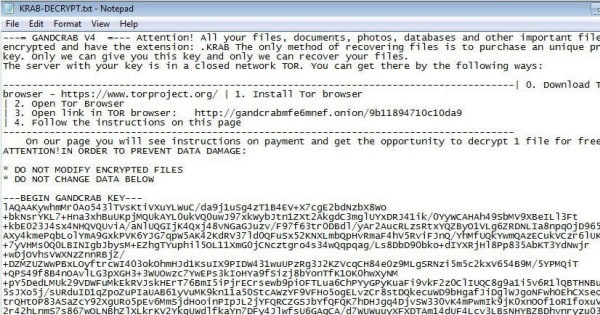
The danger is that a user will be duped into unarchiving the .EGG file, and click on the .LNK files, activating the malware. Files on the victims’ PCs will be encrypted and have a .KRAB file extension appended.
If you want to recover your files, and don’t have access to a secure backup, you may feel forced to visit the visit the ransomware’s payment site and pay the ransom to the extortionists who infected your computer.
I don’t think the .EGG archive file format is popular in any country other than South Korea, and most of the world’s computer users probably don’t have access to a tool like ALZip to unlock the malicious code contained within the poisoned .EGG files.
But we would all be wise to remember that ransomware like this doesn’t have to be delivered via an .EGG file, and could be easily used to attack home users and businesses in other parts of the world… particularly if whoever is targeting South Korea in these attacks chose to turn their attention elsewhere.



