A Linux threat known as NyaDrop is exploiting a lack of security in Internet of Things (IoT) devices to infect them with malware.
A NyaDrop attack begins with the threat attempting to brute force the default login credentials of internet-exposed IoT device running Linux. It does so by running through its list of stored usernames and passwords, a collection which is no doubt similar to that of the Mirai botnet.
In the event a user has changed the device’s credentials from their default setting, NyaDrop could fail to authenticate, or it could take several times to login.
Alternatively, the threat could gain access on the first attempt.
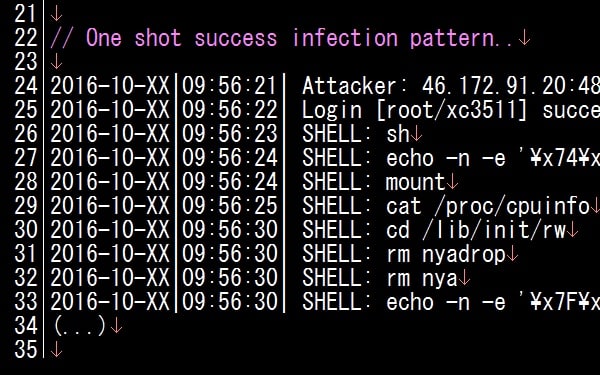
The MalwareMustDie blog notes that successful authentication leads to the installation of NyaDrop, a lightweight binary which drops other malware onto the affected machine:
“The successfully installed malware file in the MIPS system is the Linux malware backdoor and dropper, I call it as ELF Linux/NyaDrop malware, with the function to open an internet socket (AF_INET) to remotely connect to the remote host for receiving data of any Linux executable stream intended to infect the previously Linux/NyaDrop compromised machine. The stream of received data to then be saved as ‘nya’ ELF malware file and then to be executed by Linux/NyaDrop with its permission privilege on the targeted MIPS cpu architecture device.”
NyaDrop specifically targets the MIPS system because it’s a 32-bit CPU architecture that DVRs, CCTV cameras, and other vulnerable IoT devices commonly employ.
Those systems are updated now and then. That’s why Nya comes with a fail-safe: it self-deletes each time NyaDrop logs into the MIPS system, at which point in time the threat updates its malware to stay one step ahead of security researchers.
Such a technique makes for some elusive malware and, as a result, a poor rate of detection among anti-virus solutions.
NyaDrop isn’t utterly elusive, however. It has been spotted before.
In fact, NyaDrop first surfaced back in May. At that time, the threat was so poorly designed that it failed to complete its installation of Nya onto an infected device.
That all changed in September 2016.
When the Mirai botnet brought down Brian Krebs’ website, a new and improved NyaDrop surfaced. No doubt its actors are hoping to use their threat to abuse the vulnerable IoT sector.
Many computer criminal groups must feel the same way. And with the public release of Mirai’s source code, they now have a way to realize their attacks.
With that in mind, it’s crucial that users change the default login credentials on their IoT devices. Customers should choose a unique username and a strong password for each of their devices. Doing so will help them stay safe against NyaDrop and a host of other IoT threats yet to come down the pipe.