Cisco has announced it will be releasing a patch for a zero-day vulnerability exploited by a group of NSA hackers.
On 16 September, the US technology company based in San Jose, California published an advisory for the CVE-2016-6415 vulnerability:
“A vulnerability in Internet Key Exchange version 1 (IKEv1) packet processing code in Cisco IOS, Cisco IOS XE, and Cisco IOS XR Software could allow an unauthenticated, remote attacker to retrieve memory contents, which could lead to the disclosure of confidential information.”
Unfortunately, that means users of firewalls, routers and switches made by Cisco are potentially at risk, as IKE is part of the Internet Protocol Security (IPsec) protocol suite. It helps oversee the encryption and authentication of a communication session using cryptographic attributes over UDP ports 500, 4500, 848, and 4848.
By abusing the security issue, an attacker can remotely retrieve memory contents and potentially gain access to confidential information.
As Cisco explains:
“An attacker could exploit this vulnerability using either IPv4 or IPv6 on any of the listed UDP ports. This vulnerability can only be exploited by IKEv1 traffic being processed by a device configured for IKEv1. Transit IKEv1 traffic cannot trigger this vulnerability.”
At this time, Cisco has yet to release a patch for the security issue, although it does say it plans to do so in the near future.
Interesting… so why the advisory before the patch?
The technology company likely felt the need to address the vulnerability after it found exploit code targeting the flaw in a data dump released by a mysterious group known as “The Shadow Brokers” back in August.
The Shadow Brokers claim to have hacked the Equation Group, a threat actor who many believe has conducted various cyber espionage campaigns on behalf of the NSA over the years.
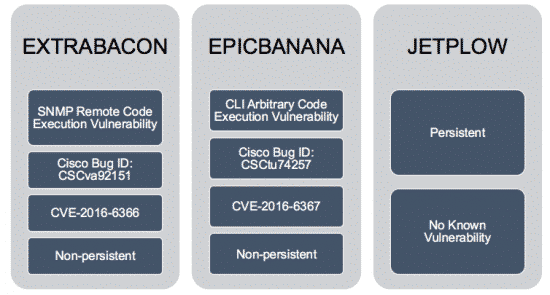
Shortly after news first broke about The Shadow Brokers, Cisco confirmed two flaws that the Equation Group allegedly targeted in three of its exploits: EXTRABACON, EPICBANANA, and JETPLOW.
Cisco now knows NSA hackers previously leveraged CVE-2016-6415 in another exploit known as BENIGNCERTAIN. Given that history, it’s safe to assume others might now begin actively exploiting the flaw.
Pending Cisco’s upcoming patch, sysadmins don’t have the option of implementing a workaround because there aren’t any. Instead they should use an intrusion prevention system (IPS) or intrusion detection system (IDS) to try and block actors from exploiting CVE-2016-6415.