 Researchers at Russian anti-virus company Dr Web believe that they have uncovered a new botnet, which has recruited thousands of Mac computers.
Researchers at Russian anti-virus company Dr Web believe that they have uncovered a new botnet, which has recruited thousands of Mac computers.
According to their report, the sophisticated malware – which they have dubbed Mac.BackDoor.iWorm – has infected more than 17,000 computers running OS X.
Unfortunately, what isn’t presently documented is how the malware spreads – but the consequences can clearly be serious.
Like any computers that have been recruited into a botnet, Macs that have been hijacked in this attack could have information stolen from them, further malware planted upon them, or be used to spread more malware or launch spam campaigns and denial-of-service attacks.
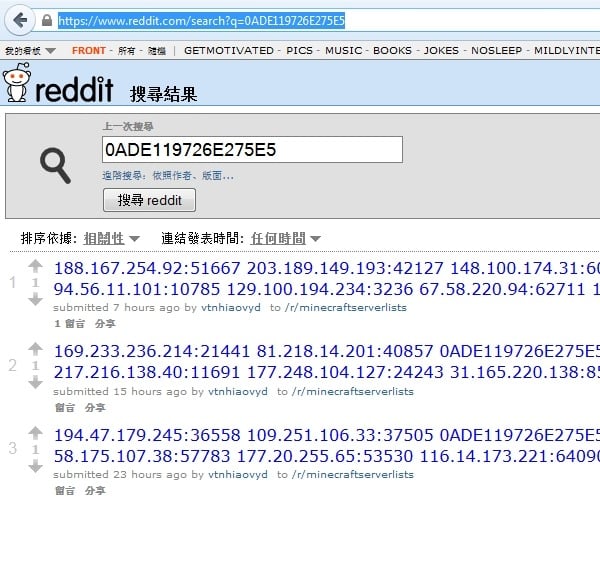
Fascinatingly, compromised computers receive commands from servers under the control of botmasters, using information posted in messages on Reddit as a navigational aid:
Then Mac.BackDoor.iWorm opens a port on an infected computer and awaits an incoming connection. It sends a request to a remote site to acquire a list of control servers, and then connects to the remote servers and waits for instructions.
It is worth mentioning that in order to acquire a control server address list, the bot uses the search service at reddit.com, and — as a search query — specifies hexadecimal values of the first 8 bytes of the MD5 hash of the current date. The reddit.com search returns a web page containing a list of botnet C&C servers and ports published by criminals in comments to the post minecraftserverlists under the account vtnhiaovyd.
This isn’t really Reddit’s fault of course. They’ve done nothing wrong as such, and even if they shut down the accounts that are communicating with the botnet there would be nothing to stop the hackers behind the campaign creating new accounts or using an alternative service (Twitter, perhaps?) to communicate with the compromised computers.
And it’s important to stress that Reddit isn’t spreading the infection – it’s simply providing a platform that is helping the botmasters communicate with the Mac computers they have managed to infect.
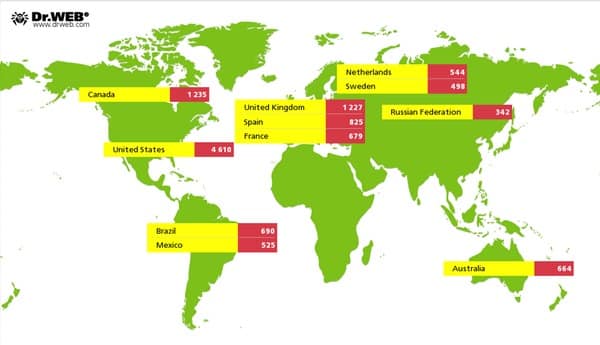
Dr Web’s research team claim that the country hit hardest by the botnet is the United States, followed by Canada and the United Kingdom.
This isn’t, of course, the first time that we have seen Mac computers infected by malware and hijacked into a criminal botnet, and it isn’t anything like as big so far as the notorious Flashback worm which hit more than 600,000 Mac computers in early 2012.
But it is another timely warning that Mac users shouldn’t be fooled into thinking they are somehow immune from computer security threats. An anti-virus product should be part of your arsenal, if you value your privacy and the data you store on your Apple computer.
In addition, keep your computer patched with the latest security updates – both for the underlying OS X operating system, but also for commonly targeted software such as Adobe Reader, Flash and Java.
More information about this particular threat can be found on Dr Web’s website.
Update: The guys at Bitdefender have been in touch, offering readers of Graham Cluley Security News, a special deal whereby you can get six months’ free protection with their Mac anti-virus product. You can check it out here.
Bitdefender tells me that Bitdefender Antivirus for Mac detects the malware as Mac.OSX.iWorm.D, Mac.OSX.iWorm.C, Mac.OSX.iWorm.B, and Mac.OSX.iWorm.A. Clearly a few different versions of the attack have already been seen, and users would be wise to keep their Mac anti-virus products updated as it wouldn’t be a surprise if there were more to come.
The Bitdefender offer runs out at midnight on
If other vendors have similar deals, please leave a comment below so Mac users can check it out.


I'm disappointed.
Headline: "…with a little help from Reddit"
Article: "This isn’t really Reddit’s fault of course … it’s important to stress that Reddit isn’t spreading the infection."
But it's only necessary to stress that because you started off the article claiming that Reddit is helping the infection! It's like saying that a chainmail scam duped thousands of people, with a little help from the post office.
You have really high quality posts and I am satisfied subscriber, but please don't fall into the trap of deceiving click-bait headlines. You're better than that.
Thanks for the feedback Scott, and I appreciate you leaving a comment.
I'd much rather you told me you were disgruntled than left for some other corner of the internet and never darkened the doorstep of GCHQ again. :)
Maybe my headline was sloppily worded – I'm not sure it was, but I'm open to criticism on that, and would be happy to hear suggestions from others on how I could better phrase it.
What I wanted to get across in the story were two interesting aspects: firstly, new and apparently widespread Mac malware. and, secondly, the use of Reddit for botnet command-and-control purposes.
Of course, over the years we've seen Twitter used for botnet c&C on many occasions (here's an early example: http://www.arbornetworks.com/asert/2009/08/twitter-based-botnet-command-channel/ ) but many folks may be unaware that sometimes Reddit can be unwittingly called into action to help the bad guys too.
Maybe I should have got onto the Reddit part of the story earlier in the piece, but I felt the Mac malware part was probably the thing which would concern potential victims the most.
Graham, don't worry about it. There'll always be some armchair critic who complains when a headline doesn't give 100% of the information from a story — despite the obvious limitations in size.
My response is, "Let's see you try crafting a better hed."
What is, "hed"? Are you so lazy you cannot spend the extra effort? Really? Are you employed? if you are, I feel sorry for the company. Your response is empty in its response. It reads as though you are 15 years old. You assume the reader understands your position, how can we? You provide no support to your response.
Just in case dwanewil isn't the troll he appears to be, my credentials ought to be obvious to anyone who bothers to click on my name. As to the standard newsroom abbreviation of headline, let's call it a shibboleth, shall we?
"A little help" = accurate. => Not clickbait.
Hi Graham
What is a good anti-virus program for an iMac? Every time I have asked at the Apple store if it is necessary to have one, they say no. I have thought it weird that supposedly there are no viruses that can infect a MAC. So if there is something out there that I can try, preferably a free version, I will do so. Thanks.
AV-Comparatives just ran an indepth comparative test of anti-virus products for Mac, finding that there were some good free solutions out there. Indeed, some of the products weren't just good at dealing with Mac malware, they also did a neat job at stopping Windows malware too!
You can read a summary of the results here: http://uk.pcmag.com/opinion/35401/mac-antivirus-products-prove-effective-in-whole-pr
and full report here: http://www.av-comparatives.org/wp-content/uploads/2014/09/mac_review_2014_en.pdf
If anyone has a recommendation, hopefully they'll also leave a comment. Thanks for asking, and let us know how you get on.
Avast is decent. I've used it for a while and it's pretty solid.
Sophos Anti-Virus Home Edition is free and effective.
I haven't seen anything anywhere about how a machine might get infected with this Mac.BackDoor.iWorm. I suspect the user has to do something stupid, as is usually the case.
It really isn't necessary to use anti-virus on Mac OS. I've been using Macs since 1986, and have never had a machine become infected. Just use a little common sense, and be careful what you install. If told you have to first download and install software before you can see a video, for instance, it's probably a bad idea.
I would recommend Little Snitch, though. This app prevents any process from connecting to the internet without your permission. It would not only prevent your machine joining a botnet, it can prevent "legit" apps known for transmitting personal data from phoning home.
Saying people don't need antivirus if they're "smart" is a bit self-congratulatory and extremely short sighted. That you've never been "infected" (that you know of) doesn't mean you never will, regardless of how smart you think you are.
On the other hand, if a reputable security company dubs the malware a "worm," you're probably wrong.
Hatcheck for Dr Web, anyone?
Apple thrives on ignorance and the simple minded. What makes you think everyone is like you?
You stated. "I've been using Macs since 1986, and have never had a machine become infected." Guess what, the OS had such a small market share until the past few years and now that the OS has a viable user base, hackers will focus on the OS and now hack the crap out of it. Do the math, "Windows" had a global market share in 2003 around 70% and the, "MAC" had, MAYBE 7%. If you are a hacker and you wish to make statement…..you are smart enough to understand where I am going with this.
You question? See link below…
https://grahamcluley.com/mac-malware-botnet-reddit/
I will give you this, at least you can construct a proper sentence. This is not common with most MAC users. You are an exception, sir.
iWorm is a trojan, installed by sloppy users pirating software, who have specifically changed Gatekeeper permissions to let an unsigned application run, and who also click to allow the JavaW virus daemon to run if the built-in OS firewall is enabled. The malware is indeed so scared of Little Snitch that it appears not to run if it detects the presence of a Little Snitch install.
Details on this garnered from https://docs.google.com/document/d/1YOfXRUQJgMjJSLBSoLiUaSZfiaS_vU3aG4Bvjmz6Dxs/edit?pli=1 (unsourced, so take with grain of salt).
Is disabling the built-in firewall stupid? A little. Is turning off the default Gatekeeper setting to only allow signed apps and Apple-signed apps from the Mac App Store stupid? Yes. Is downloading and running pirated software dumb? Definitely. Three strikes, and you're owned.
You're falling for a dangerous fallacy then, sudon't. I'll point two things out in increasing order of significance:
1. There is a reason mail servers (example) use antivirus software. Do they? Yes, they do. I know because I maintain servers (mail included). And no it isn't Mac but understand that MacOSX is based on BSD and NeXT, both of which are Unix derivatives. And if you think that malware does not attack these systems, see point 2.
2. Does the name Robert Tappan Morris mean anything to you? No? Well look up the Morris Worm. One of the earliest examples of – and certainly the most notorious – worms. This was in the late 80s, I might add. I suggest you find out which systems it affected. In addition, check out the Ramen Noodle Worm and there's others too (one comes to mind but the name is at the tip of my fingers…). In fact, a simple shell script could easily open a – and yes this pun is very well intended – huge can of worms. It might not be basic to you but anyone with enough experience can do it. Privilege separation helps but not when people (and people do this despite being told by people like me, how bad an idea it is) log in as root just so they don't have to worry about it when they want to install software/do something requiring root access. And even without root you can still wreak havoc on your own account, mark my words there.It is so easy it is scary. Unix was never designed with security in mind. Fact.
The fact that you don't see as much malware is because there are less Macs (and more generally Unix systems) which means the target size is smaller. That is, they're smaller size for home/desktop users. But believe me, it exists. Besides that: rootkits and other attacks.
That's a fascinating way to send commands to a botnet. They really will think of anything, won't they?
Is there a good detection for this, like a process I can scan my computer for?
So both MS pcs and Macs both need AV- so much for that Apple propietary price. Guess I'll stay with free debian but how does this all make any sense? The FREE is looking to be superior.
Hey fundamentalist,
Shellshock bash bug affects *nix machines. I guess Linux needs an AV too.
Correct, fudge.
Although not because of (that) bash (which is primarily Linux – indeed it is GNU bash and GNU is very much Linux) bug.
elmer: clamav comes to mind. Is often used for mail servers. But there's others.
Free is best, as in Windows Defender built into Windows 8+
I advise new Win8 owners to remove any third party AV products, which disable Windows Defender by design. Once removed, Defender takes over. Negligible footprint, always up-to-date, it takes care of the nasty stuff excepting crapware that users deliberately but inadvertently install themselves. These types of annoying programs piggy back with questionable "Free Bingo" programs and such, but are easily removed after the fact via Control Panel.
Of course, if you're surfing pr0n, all bets are off.
OS X is free. It's been $0 since OS X 10.9 was released in October 2013.
It's understandable that you may have overlooked that since it came out after the last stable Debian 7 build. OS X 10.10 will probably beat Debian 8 to release. You might want to check it out one of these years when you upgrade. I mean, if you're into the upgrade thing.
Really, Apple software free? Surprised. Any way, I should just remind you that MacOSX is BSD and NeXT whereas Debian is a Linux distribution. Mind you I have nothing against BSD – have fond memories of it, as well as other Unix systems. But there is a difference. For example, as a system (and application) programmer, I wouldn't touch MacOSX with a barge pole. There's other things that might seem not a bother or too little difference, but they do matter. Here's another thing: my servers' OS has an product life time of 10 years, which is very important for servers (they backport security fixes and there is no risk compared to other systems and in fact there are less and it is more stable too).
I think what I'm getting at – and by no means am I suggesting your view is wrong/whatever – is that we all have different needs and the only similarity to Linux and MacOSX is its origin. Out of interest (if you see this): does MacOSX work on hardware other than Apple's ? Or did Apple actually end up with non proprietary hardware ?
How about a "here's how you can check if your system has been compromised" paragraph?!?
Answering from TFA:
Criminals developed this malware using C++ and Lua. It should also be noted that the backdoor makes extensive use of encryption in its routines. During installation it is extracted into /Library/Application Support/JavaW, after which the dropper generates a p-list file so that the backdoor is launched automatically.
I don't like to use '6 months' Bitdefender Antivirus for Mac.
Can Sophos Anti-Virus for Mac(100% free) detect this malware and removing this malware from a computer well?
Combine "Researchers at Russian anti-virus company Dr Web" with the fact that 90% of hacks and bonnet attacks come from Russia or Eastern Europe (via Russia) and perhaps a few questions might be asked:
1. Is there any connection between the hackers in Russia Vs "Russian Anti-virus companies" ? Has the "Russian Anti-virus company" been audited by an independent agency to verify that they are not working both sides of the aisle ?
2. Isn't this a catch-22. You get the latest Anti-virus from a "Russian Anti-virus company". Soon the hackers figure this out and introduce a malware that is not included in "this years" anti-virus database from the "Russian Anti-virus company" – so you have to renew your subscription to the anti-virus database and guess who gets to profit ?
3. Computers can NEVER be 100% safe unless they are disconnected from the Internet, with no data going in or out from the computer. This is practically impossible. So it is theoretically possible to infect any kind of system available to the consumer. So why should the consumer bother ? Its is the responsibility of the computer manufacturer. In this case, I trust Apple more than others because I know that Apple makes both the hardware and OS – they have a better (not 100%) chance of preventing this in the consumer space.
To reiterate, these bombastic headlines from self-styled "security" researchers always lead to the final question: "Show me the money!" – both for the malware makers and the "researchers" themselves.
1. There are many independent reviews (years and years) of the antivirus software (and security suites) out there.
2. This applies to everything in life, computers and otherwise. Something else: heuristics (as one example). Perfect? No but it helps.
3. Wrong, the computer disconnected is STILL not 100% safe. Not only is there keyloggers that can be attached to the keyboard, you also have to consider theft of equipment (including removing the harddrive). Computer is locked up you say? Does lock-picking mean anything to you?
Blogger thinks hmm what am I going to do today? I know, I'll read some internet sites then take to the comment section to call the other post writers names and make fun of them. I'll tell them how much smarter I am than they are. I'll tell them they should have clicked on my profile to see just what an expert I am. All my TRUE details are there for all to read, if only they would take the time.
STFU. If you dont like it move on or do it better yourself and prove just how great you are. No one cares what you think in the comment section you …..wait for the name calling….. Troll . Oh no, some you have never met and never will just call you and mybe your mom a name. Now back to the playground kids.
SAD.
This looks like an example of another story being rewritten by bloggers looking for hits and not bothering to fact check.
The article below certainly seems to indicate most bloggers missed the important facts.
http://fairerplatform.com/2014/10/iworm-worm-infected-find/
Would like to hear the author's perspective after he reads the above article.
Bottom line, the real story seems to be about users stealing software infected with a trojan. But that's not much of a headline. Add Apple and Reddit to the story and now people read what you write.
If I am not mistaken, the Mac needs to have UNIX remote services enabled, i.e. Settings>Sharing>Remote Login <enabled>, (or Remote Management), which it is not enabled by default, and most home users will not enable this. ("Remote Login lets users of other computers access this computer using SSH and SFTP.") ("Remote Management allows other users to access this computer using Apple Remote Desktop".). This feature is to allow someone to access their home Mac from work, or work Mac from home.
I've had Macs since 1998, sometimes let people like you tell me I need virus protection, whenever I've used such programs, nothing has ever been found. Macs don't get viruses, they are protected at the core of Mac OS X (any version, it was built this way). That's not to say there are not other vulnerabilities, but, Apple addresses them pretty quickly with security updates, typically covering the last 3 or 4 generations of Mac OS X.
Now, a Mac running Windows, that might be susceptible to viruses, at least for the Windows partition, but, not my expertise, haven't used windows for a few years, and that not on a Mac.
"This feature is to allow someone to access their home Mac from work, or work Mac from home." …I must add, and (only with this feature enabled), the person accessing the Mac remotely must also have the administrative password to gain access
You are quite wrong indeed. Malware does exist for non Windows systems.
By the way, needing root password for remote login is worse than non-privileged user first. In addition, password logins (remote) is less secure than keys with pass-phrases. And needing root password for remote login is not the best of ideas (I'll spare the details).
And you say Apple addresses security problems quickly? How come it took them some days to release shellshock fix? I had mine already patched (both CentOS and also Fedora Core) before it was even announced to the public. Days is not quick. Even a day is not quick especially when you have the fix already there.
What would have been helpful is how to check to see if you're infected without spending money (or using trial versions) of AV software.
http://www.techtimes.com/articles/17188/20141004/mac-users-at-risk-of-iworm-os-x-malware-infecting-computers-via-reddit.htm
To check if your Mac has been infected by iWorm, from the OS X Finder tab navigate to Go > Go to Folder. Next, type /Library/Application Support/JavaW. If your PC is unable to find the said folder you are safe. However, if you do locate the folder, use an anti-virus to remove iWorm from your drive.
If that works for you, that's great.
But bear in mind that it only helps you detect one particular piece of Mac malware, rather than all of the Mac malware in existence.
And also don't forget that you may want to regularly perform that test, as it may be that you are unfortunate enough to get infected by this malware *after* you run the test.
The beauty of an anti-virus solution is that it protects against many different pieces of malware, automatically updates itself to protect against new threats, and doesn't demand any technical knowledge on the part of the user.
For most Mac users, I suspect that running an anti-virus program is a better choice.