A lot of folks are going around at the moment telling the public to change all of their passwords in response to the serious Heartbleed internet security bug.
For instance, here’s what the Tumblr website (owned by Yahoo) has told its users:
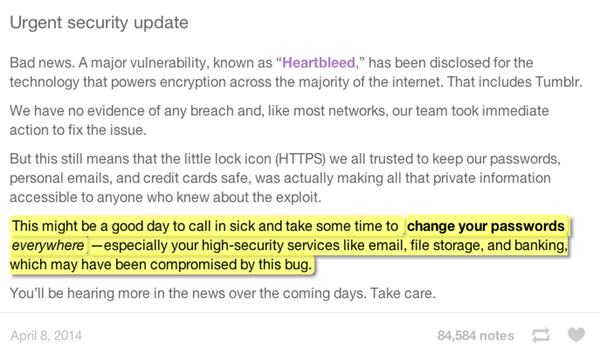
The emphasis on one particular paragraph was added by me. And it’s this section which I have a concern about:
This might be a good day to call in sick and take some time to change your passwords everywhere – especially your high-security services like email, file storage, and banking, which may have been compromised by this bug.
That’s awful advice.
You should only change your password in response to the Heartbleed bug after a website or internet company has:
- Checked to see if it is vulnerable
- Patched its systems
- Grabbed a new SSL certificate (having revoked their previous one)
- Told you it is fixed
Ideally they would initiate a mandatory change of passwords at that point. (By the way, when you do change your password, remember to also enable two factor authentication if the website or service offers it – as it will increase your overall level of security in the long run).
The danger is that if you change your passwords *before* a website has been fixed, you might actually be exposing your credentials to *greater* risk of being snarfled up by people exploiting the vulnerability in the buggy versions of OpenSSL.
Don’t forget – there are an awful lot more people now testing to see how well the vulnerability can be exploited now that details are public.
Sadly, mainstream media are proving to be a little guilty of parroting the advice of the likes of Tumblr.
Check out this BBC News article, for instance, entitled “Heartbleed Bug: Tech firms urge password reset”.

Again, I added the emphasis to the news story.
You have to scroll way down the article before you realise that actually you *shouldn’t* change all your passwords, but instead wait until a website has fixed the flaw.
And, if a website you use hasn’t made clear if they have fixed the problem (or indeed if they were ever vulnerable) then the best thing you can do is badger them into telling you.



Is change passwords the best advice we can give?
We have long known passwords are dead as a viable security technology. Rather than tell everyone to change their passwords – why not suggest upgrading to two-step verification or two-factor authentication instead? It’s almost as easy, and takes just about as long as changing your password to set up on most sites.
It may not 100% solve the issue, but it significantly reduces them.
They never were viable if you want to be strictly technical. The reason they are usually the weakest link in the chain is they are created by (and often written down) by humans, which is indeed the weakest link of them all. Even back in the day, passwords were so weak that if you could grab a password file (which an old apache bug allowed, for instance… not the only one and I can think of even worse exploits – some that allowed anyone to log in from anywhere without a password) you could almost assuredly get the password (even if salted and hashed like Unix for example, before passwords were shadowed) through dictionary attacks. And two factor is all fine and dandy but it is nothing new either. Still, not every site has that and not every person has the hardware to do it (e.g., not everyone has a mobile phone, might be hard to believe but it is true; personally phones drive me much more mental than I already am — a scary thought even). Of course, there is securid cards and those are ancient too so while it is true that you should have more than one layer of defence, that is how it always has been and changing passwords is essentially changing the weakest link (unless you want to get into semantics – i.e., social engineering) and has always been that way. To be fair to you – I realise how that this might seem to be an attack and I don't mean it to be hence this part – you are exactly correct in that passwords are not enough and that there is no 100% but I fear they are still necessary (which I do recognise you recognise this too). Best thing would be for corporations to start:
– sanitising input (SQL injection anyone? I'll not name any company like Sony….). Irony here: the heartbleed bug was related to a buffer overflow which is often abused by way of not having sane input (or making sure to not go out of bounds). The reality though is this: all programmers have done this (be it from making the mistake of programming while exhausted or simply miscalculating [off by one error comes to mind]). I'm guilty of this too and on programs that are running for days (eg servers) they can be especially ugly if not used as an attack (well, that's ugly too but I mean debugging, for example, a crash – memory corruption in general is a real thorn in the side of programmers when they come across it). Programmers are only human though. Saw someone on DSLreports railing against the programmers as if they should have never allowed this but that person is either: arrogantly in denial about making a programming mistake (of such kind or any kind) or is not a programmer (even if they think they can program or could learn to). So, while this is serious, I'm not surprised either.
– having multiple layers of defences (this includes but is not limited to: firewall [Note: NAT isn't a firewall and is not a security mechanism; it only appears that way but you can actually still get to a NATd host and NAT is not ingress and egress filtering so may as well do it properly], bastion hosts, dmz [note: not in the sense that home routers think of – I'm referring to DMZ in the computer security context], antivirus/malware, IDS, etc.), not counting authentication.
– multiple layers of authentication (keys, passwords and pass phrases, one time codes like you refer to, etc.)
– auditing. lots of it. including log files (though those aren't perfect but what is?)
Unfortunately, I have been into security for far too long to know that really, this won't happen. It is sad, its unfortunate, but it is reality. The same mentality exists in security of countries and locations too: drop guard down, attacked, then raise guards for some time. Deem it safe then drop guard down and then get attacked again. Security is an all the time thing. Consider it a constant boolean and specifically constant boolean that has the value of '1' i.e., on. At least, ideally that is how it would be.
In the end though: correct, more layers is better than less layers. And of course, Graham writes about this quite frequently.
I was going to write about this on one of my sites but it — not surprisingly as I am very lazy at times especially since this is not my job — seems Graham has beaten me to it. To which I can only be glad of. Indeed, not only should you find out if the site in question was vulnerable, you should wait until it is NOT vulnerable and everything else (e.g., new certs) are in place, before resetting (read: CHANGING) your password. In fact, I would argue that unless new certs are generated then it doesn't matter what the server is running as far as openssl is concerned: if it was running a vulnerable version then it is vulnerable until ALL have been fixed. I would suggest 'Shame on tumblr …' except that as Graham has pointed out, companies generally do not breathe or think in terms of security so they assume they know best whereas they should be always vigilant, always thinking as if they were doing the attack and above all have staff that actually can do this if they cannot themselves do it (most often the case).
Each commenter above me has excellent points. Graham, yours summation is a little lacking. I love your work, and generally trust your judgement, but passwords are nearly free. It took me less than 30 minutes to change my critical passwords last week, and I'll spend another 30 minutes this week and again next week changing them again. I find <90 minutes a reasonable investment of my time for the security it grants. Especially when I'd be changing this small set within a few months anyhow.
I see your point about waiting till services are patched, but I'm not going to wait around for an announcement that my creds may have been in memory when a site was compromised.
I've already set up two-factor auth where I can, and hope that more providers will get on board in the coming weeks.